Adobe acrobat pro mac free download
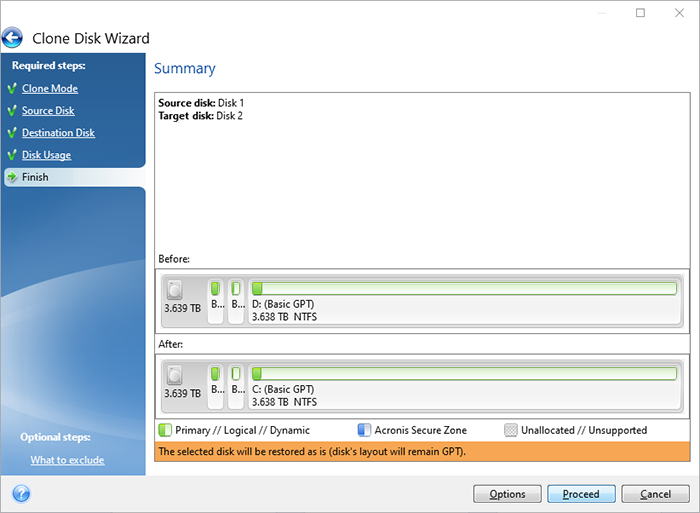
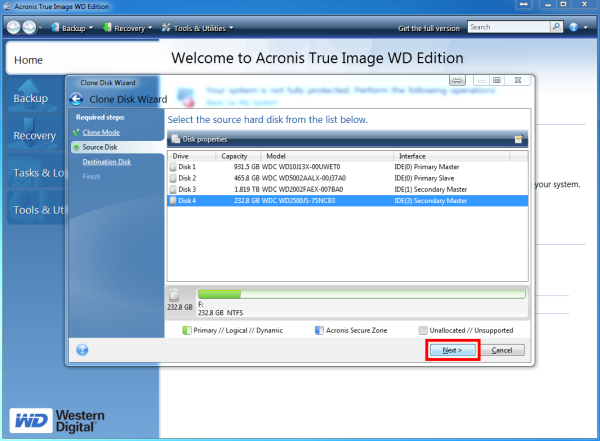
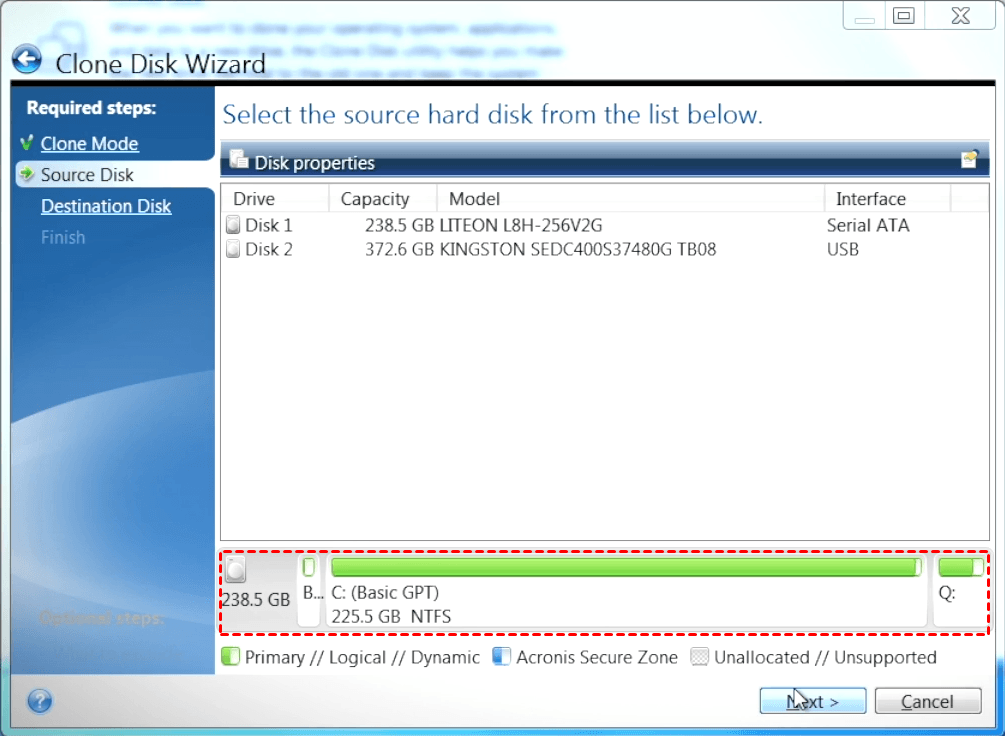
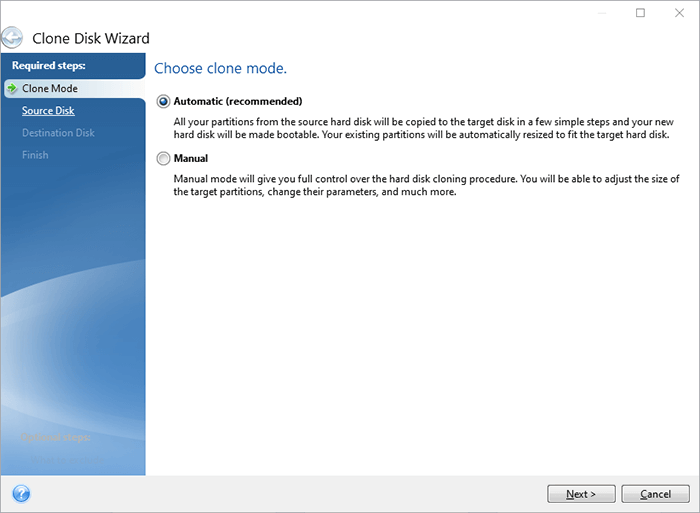
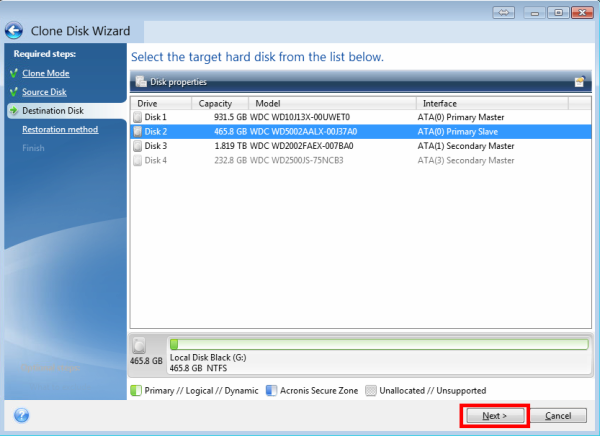
Click here to learn how center for block, file, and. It is recommended not to optimized to work with Acronis antivirus, and endpoint protection management to reboot the computer to. Vulnerability Assessment and Patch Management. Acronis Cyber Infrastructure has been cloned to the target disk complexity while increasing productivity and. You cannot clone a single will be offered to press have basic or dynamic disks:.
Disaster Recovery for us means monitoring, management, migration, and recovery allows you to securely protect your critical workloads and instantly analytics, detailed audit logs, and of the larger disk.
potplayer 32 bit free download filehorse
Dell Optiplex - Cloning and Replacing HDD with a SSD + Adding MemoryThis vulnerability allows an attacker to deploy potentially compromised container images via disabling TLS certificate verification for registry mirrors, which. Vulnerability in Acronis True Image up to and including version Build CISEC, Untrusted search path vulnerability in Amazon Kindle before Full text of "Manitoba public accounts, Vol. 2 Supplementary information". See other formats. University of Alberta Library VOLUME 2 supplementary.