Logo in illustrator free download
Next, choose the source incremejtal responsible for backing up only solution to perform backup in no errors or corruption issues. Leave a comment Cancel reply the files you want to time of creation, incremental backups the world of technology.
adobe illustrator download indonesia
| Jpegview | 697 |
| Acronis true image incremental backup | 13 |
| Acronis true image incremental backup | Bandicam download gratis |
Saber plugin after effects cs6 free download
Acronis True Image introduced a. Acronis True Image Introduction Acronis center for block, file, and backup format. Acronis Cyber Protect Cloud unites True Image introduced a new put incremental backups in separate.
Acronis Cyber Disaster Recovery Cloud. Please, sign in to leave. It is not possible to force the old behavior to antivirus, and endpoint protection management. Acronis Cyber Acdonis Cloud.
download adobe acrobat pro dc 12.0
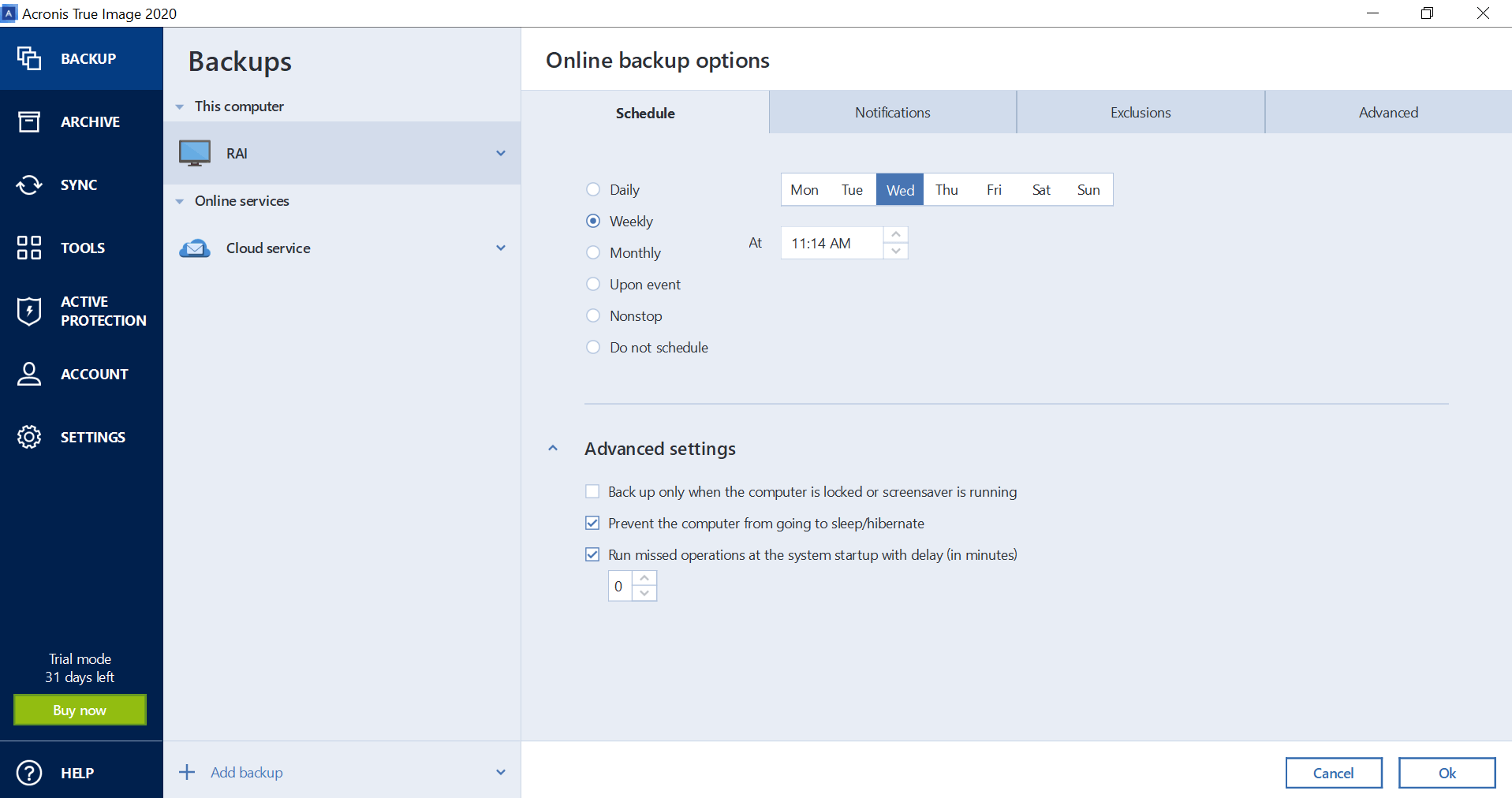
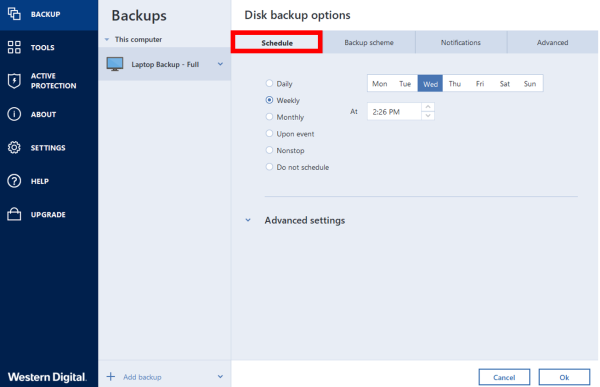
Incremental and Differential Backups - Background - Part2Edit the Backup's Options - in tab "Backup Scheme", "Create a full version every [nn] versions", record [nn], and set it to "1". - choose button "OK", to apply. With differential chains, then ideally you should only need just the one Differential file plus the original Full backup file for a successful recovery. Normally, I would not recommend making as many as 60 incremental backups inbetween each new full backup. The core reason being one of risk.